Introduction
The proliferation of fake credentials has transformed certificate verification from an optional safeguard into a business necessity. Employers discover fabricated degrees during background checks, universities encounter forged transcripts in admissions processes, and professional certification bodies face reputational damage from counterfeit credentials circulating in their industries.
Certificate verification systems address this fraud epidemic by providing authenticated methods to validate credential authenticity. These platforms replace vulnerable manual verification processes with tamper-proof digital systems that confirm certificates instantly while maintaining permanent audit trails. As credential fraud becomes more sophisticated, organizations increasingly recognize that traditional verification methods cannot protect against modern forgery techniques.
This comparison examines how certificate verification systems work, the security methods they employ, and the features that distinguish basic lookup tools from comprehensive authentication platforms. Understanding these differences helps organizations select verification infrastructure matching their risk profiles and operational requirements.
What Are Certificate Verification Systems?
Certificate verification systems are digital platforms designed to authenticate credential validity through secure, tamper-resistant databases. These systems create verifiable links between issued certificates and authoritative records, allowing third parties to confirm that credentials are genuine rather than forged or altered.
The verification process typically works through unique identifiers embedded in certificates. When someone needs to verify a credential, they enter a certificate ID, scan a QR code, or search a verification portal. The system checks this identifier against its database and returns confirmation of authenticity along with credential details like recipient name, issue date, and issuing organization.
Organizations relying on certificate verification systems include employers conducting background checks, universities validating transfer credits, professional certification bodies maintaining credential registries, compliance auditors confirming training completion, and online course platforms ensuring credential authenticity. MixCertificate serves these verification needs as a dedicated platform providing multiple authentication methods including QR codes, public verification portals, and API access for integrated verification workflows.
These systems fundamentally differ from certificates themselves. While a certificate represents credential achievement, verification systems prove that the certificate is authentic and was actually issued by the claimed organization. This distinction becomes critical as forgery technology advances.
Why Certificate Verification Is Critical Today
The need for robust verification infrastructure stems from several converging fraud trends and organizational risks.
Fake credentials have reached epidemic proportions across industries. Online marketplaces openly sell forged degrees, training certificates, and professional licenses. Technology advances have made high-quality forgeries indistinguishable from authentic certificates to the naked eye. Organizations cannot rely on visual inspection to detect fraud.
Resume fraud costs organizations through bad hires and reputational damage. Studies consistently show that 30 to 40 percent of resumes contain some form of credential fabrication. Without verification systems, organizations unknowingly hire unqualified candidates who claimed credentials they never earned. The downstream costs include poor performance, legal liability, and expensive termination processes.
Compliance and audit requirements in regulated industries mandate verified training records. Healthcare, finance, manufacturing, and other regulated sectors must prove that employees completed required certifications. Manual verification processes fail audit scrutiny because they lack documented proof of verification attempts and results. Certificate verification systems provide the audit trails regulators require.
Reputation damage affects organizations that fail to verify credentials properly. When fraudulent credentials become public, the issuing organization faces questions about their verification rigor even if they were the fraud victims. Verification systems protect organizational reputation by demonstrating due diligence in credential authentication.
The verification imperative extends beyond preventing individual fraud cases. Organizations need systemic verification infrastructure that scales with credential volume while maintaining security standards.
Common Certificate Verification Methods
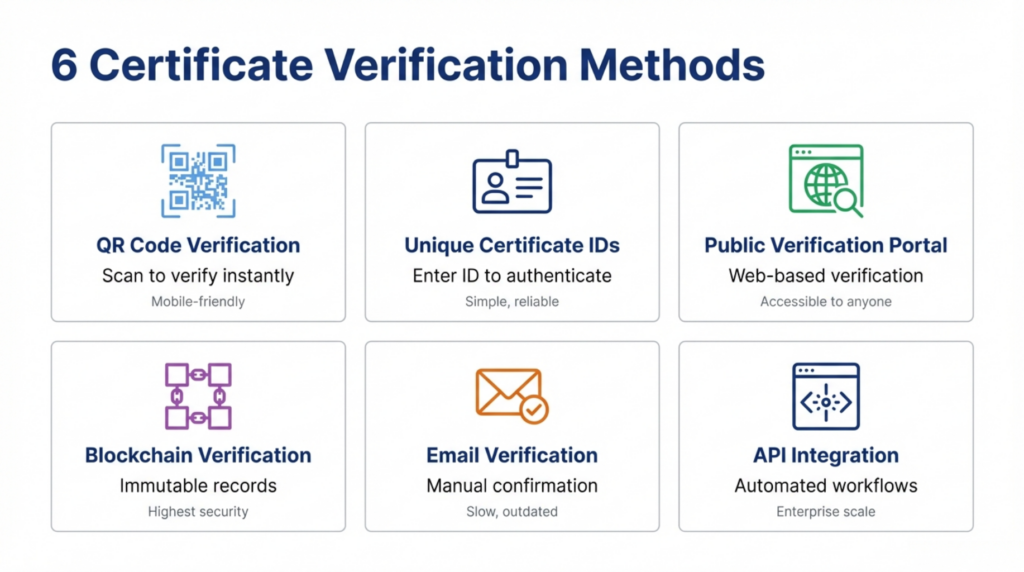
Certificate verification systems employ various technical approaches to authenticate credentials, each offering different security levels and user experiences.
QR Code Verification
QR code verification embeds machine-readable codes directly on certificates linking to verification databases. Recipients can share certificates knowing that anyone with a QR scanner can instantly verify authenticity. This method works well for printed and digital certificates, providing immediate verification without requiring recipients to remember certificate IDs.
Unique Certificate IDs
Unique identifier systems assign each certificate a distinct alphanumeric code stored in the verification database. Users enter these IDs into verification portals to confirm authenticity. This approach works reliably but requires manual ID entry, making it slower than QR scanning for high-volume verification scenarios.
Public Verification Portals
Web-based verification portals allow anyone to check certificate validity through public-facing search interfaces. Users can search by recipient name, certificate number, or other identifiers. These portals serve organizations needing to verify many credentials efficiently, such as HR departments processing applicant backgrounds.
Blockchain-Based Verification
Blockchain verification creates immutable credential records on distributed ledgers, preventing post-issuance alterations. Each certificate transaction gets cryptographically sealed, making fraud detection straightforward. While highly secure, blockchain verification requires technical infrastructure and understanding that not all organizations possess.
Email-Based Verification
Email verification sends confirmation requests to issuing organizations when third parties need to verify credentials. The issuer responds confirming or denying authenticity. This method works but introduces delays, requires manual effort from issuers, and lacks the scalability that automated systems provide.
Platforms like MixCertificate typically support multiple verification methods simultaneously, allowing certificate recipients to choose their preferred authentication approach while ensuring issuers maintain comprehensive verification infrastructure regardless of method selected.
Platform Comparison: Verification Features
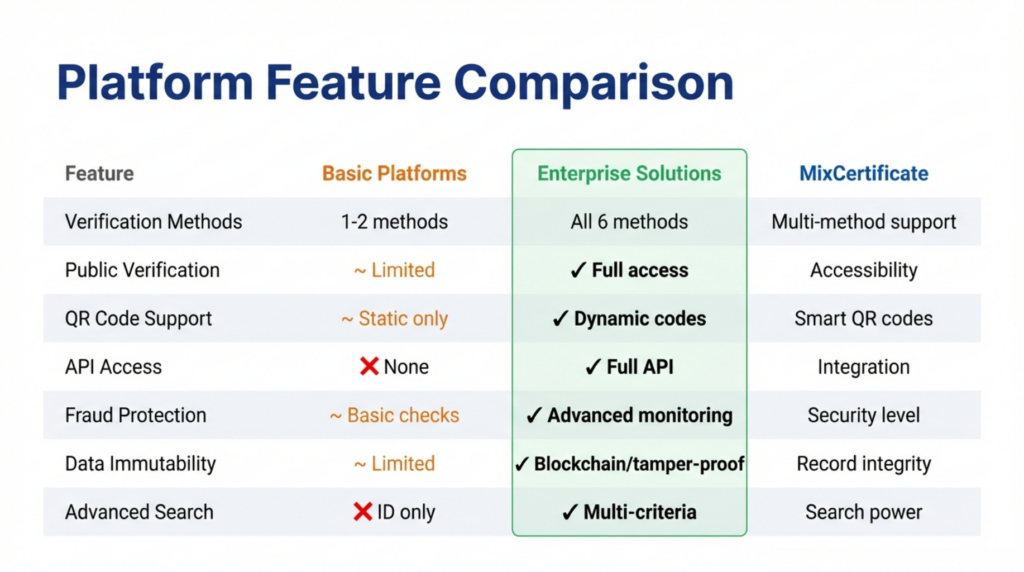
Certificate verification systems differ significantly in their security features, accessibility, and technical capabilities. Understanding these differences helps organizations select appropriate platforms.
Verification Methods Supported
Basic platforms offer single verification methods, typically unique ID lookup through web portals. Comprehensive systems like MixCertificate provide multiple verification pathways including QR codes, ID lookups, public verification portals, and API access, accommodating diverse verification scenarios and user preferences.
Public Verification Pages
Public verification accessibility determines how easily third parties can authenticate credentials. Some platforms restrict verification to logged-in users or require special permissions. Open platforms provide public verification pages accessible to anyone, enabling employers, universities, and other verifiers to confirm credentials without requesting issuer assistance.
QR Code Support
QR code functionality varies from basic static codes linking to PDFs through dynamic codes connecting to verification databases. Advanced platforms generate unique QR codes for each certificate that remain functional even if certificate design changes, maintaining verification capability throughout credential lifecycles.
API Access
API availability enables automated verification workflows integrating with HR systems, applicant tracking platforms, or compliance software. Organizations processing hundreds of verification requests benefit from APIs that eliminate manual verification steps. Platforms like MixCertificate provide robust APIs supporting bulk verification and system integration.
Fraud Protection Levels
Fraud prevention ranges from basic ID matching through sophisticated tamper detection and duplicate prevention systems. Enterprise platforms monitor for suspicious patterns like multiple verification attempts on slightly modified credentials, flagging potential fraud attempts for investigation.
Data Immutability
Immutability ensures that certificate records cannot be altered after issuance. Blockchain-based systems provide cryptographic immutability. Database-based platforms achieve similar protection through audit logging and access controls preventing record modification. This feature proves essential for credentials with compliance or legal significance.
Search and Lookup Features
Search functionality determines verification efficiency. Basic systems require exact certificate IDs. Advanced platforms enable searches by recipient name, date ranges, credential types, or multiple combined criteria. Comprehensive search accelerates bulk verification processes.
The feature comparison reveals clear tiers. Basic verification tools provide simple ID lookup. Mid-tier platforms add QR codes and public portals. Enterprise solutions like MixCertificate deliver comprehensive verification infrastructure including APIs, advanced search, fraud monitoring, and integration capabilities.
Security and Data Integrity Considerations
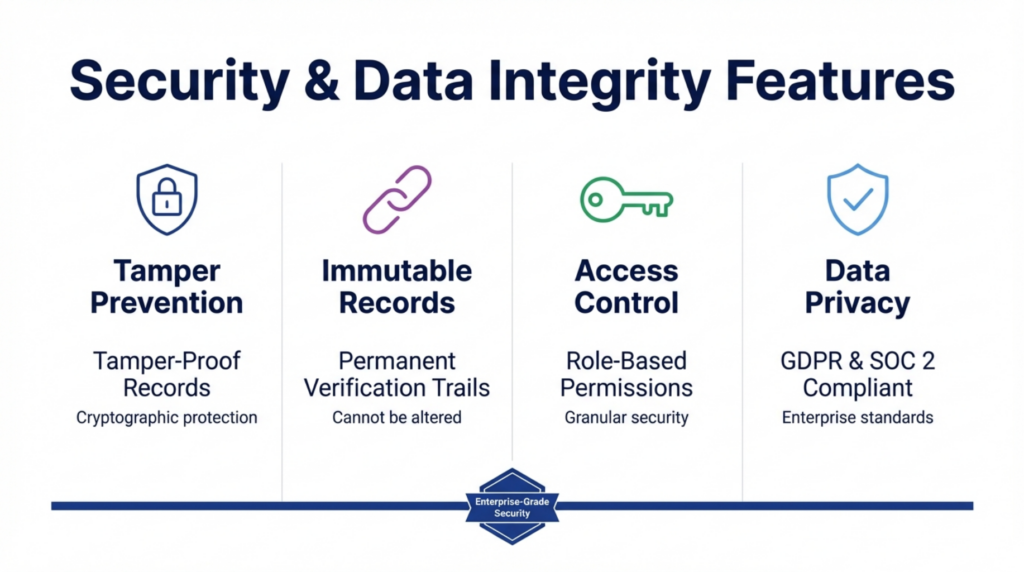
Verification system security determines trustworthiness and organizational risk exposure.
Tamper prevention ensures that certificates and verification records remain unaltered after issuance. Systems achieve this through cryptographic hashing, blockchain anchoring, or append-only databases that log all actions without allowing modifications. Tamper prevention protects against both external fraud and internal manipulation.
Immutable records create permanent verification trails that survive system migrations, organizational changes, and technology updates. When verification systems maintain immutable records, credentials issued decades ago remain verifiable using the same infrastructure. This permanence proves critical for academic credentials and professional licenses with lifelong validity.
Access control determines who can verify credentials, issue new certificates, or modify system settings. Granular access controls prevent unauthorized verification, protect personally identifiable information, and ensure that only authorized personnel can issue credentials. Robust platforms provide role-based permissions matching organizational hierarchies.
Data privacy standards govern how verification systems handle personal information. Platforms must comply with regulations like GDPR, CCPA, and industry-specific privacy requirements. Privacy-focused systems allow credential verification without exposing unnecessary personal details, balancing authentication needs against privacy protection.
Security considerations extend beyond technical features to operational practices. Organizations should evaluate verification platform security certifications, data encryption standards, backup procedures, and disaster recovery capabilities. Platforms like MixCertificate that achieve SOC 2 compliance demonstrate serious commitment to security and data protection.
Use Cases for Certificate Verification Systems
Specific organizational scenarios demonstrate why verification infrastructure matters operationally.
Hiring and background checks require employers to verify claimed credentials before making offers. HR teams face hundreds of verification requests during recruitment cycles. Automated verification systems process these requests instantly rather than requiring manual outreach to issuing institutions. This speed reduces time-to-hire while ensuring credential authenticity.
Academic credential validation allows universities to verify transfer credits, graduate school applications, and international qualifications. Registrars spend significant time on verification requests from other institutions. Public verification portals let requesting institutions verify credentials independently, reducing administrative burden on both sides.
Professional certifications need verification infrastructure to maintain credential value. When certifications lack verification capabilities, counterfeit credentials circulate unchecked, undermining the certification’s reputation. Verification systems protect certification value by ensuring that only legitimate holders can prove credential ownership.
Compliance and regulatory audits require documented proof that employees completed mandatory training. Auditors need to verify not just that training occurred but that verification evidence exists. Platforms like MixCertificate provide audit-ready verification logs showing when credentials were verified, by whom, and what results were returned.
Online course credentials face particular verification challenges because purely digital credentials seem easy to forge. Course platforms need verification infrastructure to ensure their certificates carry weight with employers and educational institutions. Robust verification transforms course certificates from participation badges into respected credentials.
Each use case shares common requirements for instant verification, minimal manual effort, audit trails, and fraud prevention that modern verification systems address systematically.
Verification Systems vs Manual Verification
Traditional verification approaches fail to scale and introduce vulnerabilities that automated systems eliminate.
Email verification requires sending verification requests to issuing organizations and waiting for manual responses. Response times vary from hours to weeks. Organizations may not respond at all if they lack processes for handling verification requests. Email creates no audit trail, offers no standardization, and depends entirely on human responsiveness.
PDF certificates cannot be verified without contacting issuers. Anyone can create convincing PDF certificates using design tools. Visual inspection reveals nothing about authenticity. Organizations accepting PDF certificates without verification accept substantial fraud risk.
Phone confirmations introduce similar problems as email verification plus additional challenges. Reaching the right person by phone takes time. Phone conversations leave no documentation for audits. Fraudsters can impersonate institutional representatives over the phone.
Human dependency affects all manual verification methods. Every manual step introduces delay, inconsistency, and error potential. Staff turnover disrupts verification processes. Manual methods cannot scale to handle hundreds of verification requests efficiently.
Automated certificate verification systems eliminate these failure points. Verification happens instantly, 24/7, without human intervention. Results remain consistent regardless of when verification occurs. Audit trails document every verification attempt. The shift from manual to automated verification parallels the shift from manual to automated certificate generation, driven by volume, accuracy, and efficiency requirements.
Platforms like MixCertificate exemplify this automation advantage by processing verification requests in seconds rather than days while maintaining comprehensive documentation for compliance purposes.
How to Choose the Right Certificate Verification System
Selecting verification infrastructure requires evaluating specific capabilities against organizational needs.
Verification speed determines user experience and operational efficiency. Systems should return verification results within seconds. Slower verification creates friction that discourages verification attempts, undermining the entire infrastructure’s purpose.
Ease of access affects how many people actually verify credentials. Systems requiring special software, complex procedures, or restricted access reduce verification rates. Public verification portals accessible through standard web browsers maximize verification adoption.
Security level must match credential importance and fraud risk. High-stakes credentials like professional licenses justify blockchain verification or other high-security methods. Lower-risk credentials may work fine with standard database verification. The security investment should align with fraud consequences.
Scalability determines whether verification infrastructure can grow with credential volume. Organizations issuing thousands of credentials monthly need platforms handling equivalent verification loads without performance degradation. Cloud-based systems scale more reliably than self-hosted solutions.
Integration support enables verification workflows to connect with existing systems. Organizations using applicant tracking systems, learning management platforms, or HR information systems benefit from APIs that automate verification processes. MixCertificate and similar platforms provide integration capabilities that reduce manual verification workload.
Organizations should also evaluate total cost of ownership including setup fees, per-verification costs, storage fees, and support costs. The cheapest platform rarely delivers the best value when fraud prevention and operational efficiency are considered.
Frequently Asked Questions (FAQs)
What are certificate verification systems?
Certificate verification systems are digital platforms that authenticate credential validity through secure databases and unique identifiers. These systems allow employers, educational institutions, and other third parties to confirm that certificates are genuine and were actually issued by the claimed organization rather than forged or altered.
How does digital certificate verification work?
Digital certificate verification works by matching unique identifiers embedded in certificates against authoritative databases. Users scan QR codes, enter certificate IDs, or search verification portals. The system checks these identifiers, confirms authenticity, and returns credential details. This process completes in seconds without requiring manual contact with issuing organizations.
Are certificate verification systems secure?
Reputable certificate verification systems implement multiple security layers including tamper-proof databases, encrypted data transmission, access controls, and audit logging. Advanced platforms use blockchain anchoring or cryptographic hashing to prevent unauthorized modifications. Platforms like MixCertificate maintain SOC 2 compliance demonstrating enterprise-grade security standards.
Can employers verify certificates online?
Yes, modern certificate verification systems provide online verification portals accessible to employers during background checks. Employers can verify credentials instantly by entering certificate IDs, scanning QR codes, or searching by candidate name. This online verification eliminates delays associated with manual verification processes requiring institutional contact.
What is QR-based certificate verification?
QR-based certificate verification embeds machine-readable codes on certificates that link to verification databases. Anyone with a smartphone can scan these QR codes to instantly confirm certificate authenticity. QR verification provides immediate authentication without requiring users to manually enter certificate identifiers or navigate verification portals.
Is MixCertificate suitable for certificate verification?
MixCertificate is specifically designed for comprehensive certificate verification across organizational scales. The platform supports multiple verification methods including QR codes, public verification portals, API access for integrated workflows, and advanced search capabilities. MixCertificate serves organizations requiring enterprise-grade verification infrastructure with fraud prevention, compliance documentation, and scalability for high-volume credential programs.
Conclusion
Certificate verification systems have evolved from optional security measures into essential infrastructure protecting organizations against credential fraud. The comparison reveals significant differences between basic ID lookup tools and comprehensive verification platforms offering QR codes, public portals, APIs, and fraud monitoring.
Organizations face increasing verification requirements driven by fraud proliferation, compliance mandates, and reputational risks. Traditional manual verification methods cannot scale or provide the audit trails modern environments require. Explore MixCertificate Pricing Plans for your Organizations and Automated verification systems deliver instant authentication while maintaining comprehensive documentation.
Selecting appropriate verification infrastructure requires matching platform capabilities to organizational needs. Speed, security, scalability, and integration support determine whether verification systems will actually get used and protect against fraud. Platforms like MixCertificate address enterprise requirements through multi-method verification, robust security, and operational features purpose-built for high-volume credential verification.